Finger Vein Desktop Reader overview
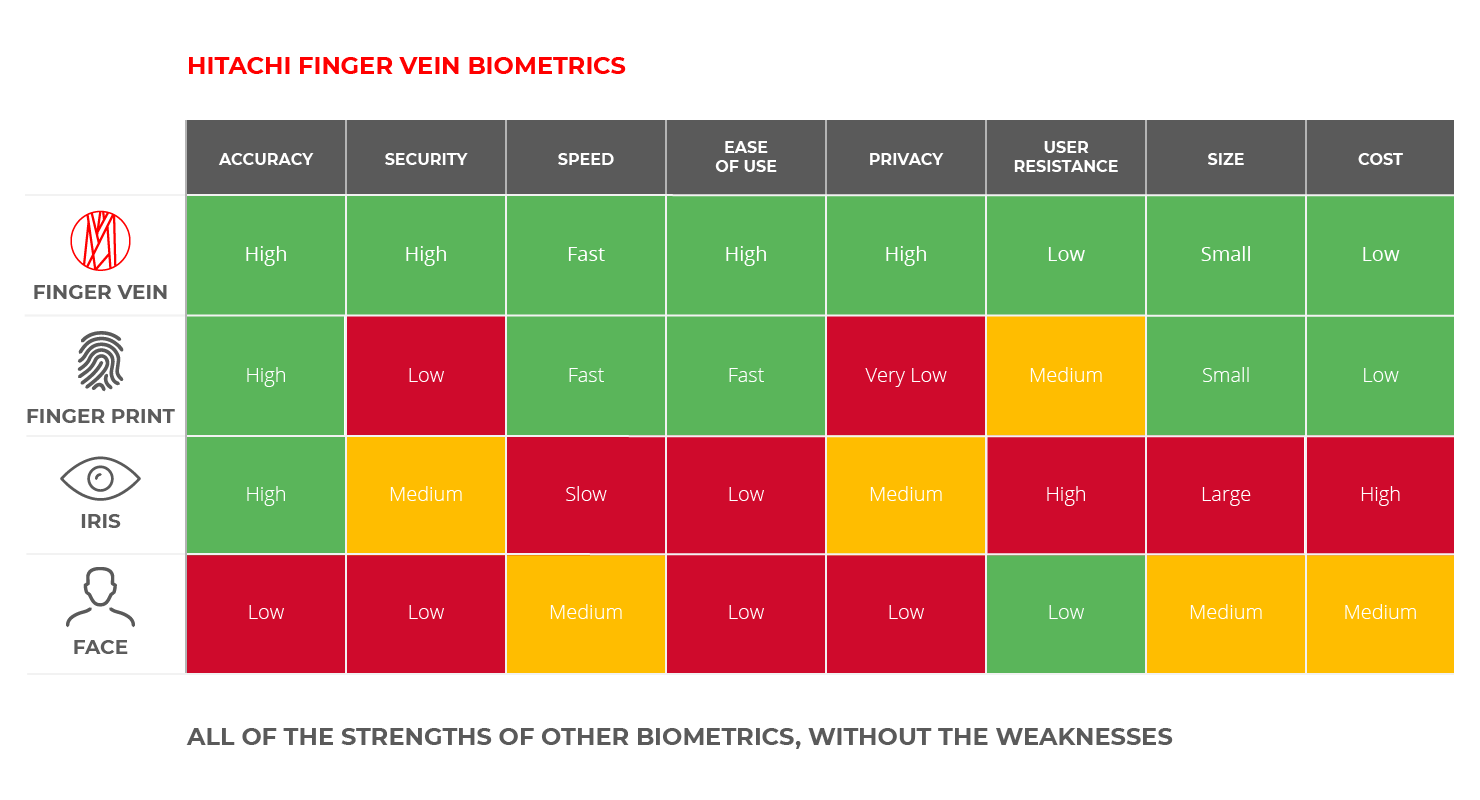
Finger vein technology is a safe, reliable, non-invasive biometric solution which provides fast and highly accurate identity authentication for access to data or secure areas.
See the H-1 Reader in action
Point of view
Users can now guard against illegitimate access or leakage of information on their computers by using the vein patterns in their fingers as their computer login.
Solutions
Identity Management – single sign on
The combined package enables organisations to implement cost-effective identity management, giving users simple access to applications without the need for multiple passwords, and without compromising security.
Time and Attendance
An easy-to-use, fast, accurate and system to record employees hours of working and site security. Suitable for organisations employing just a few people, up to large scale businesses – manages all your time & attendance and security and software requirements in one integrated security management system.
Banking and Finance
Adding biometric identification to a smart card solution enables proof that the identity of the card holder matches the unique finger Vein template of that person. This strengthens access control security by requiring two-factor authentication. Allowing identification of who is entering rooms within the building and to control access to computers and files is an essential element for all financial institutions.
Can be integrated into building and premises access control systems enabling people to open doors and even alert authorities for physical access control to restricted areas e.g:
- Vaults containing high value bearer bonds, bullion, cryptographic Keys
- Data Centres
- Secure payments areas.
Access can be tailored
- Mandatory control — four eyes, two fingers
- Discretionary control — admin can alter subordinates
- Rule based
- Organization based — an independent security policy from the implementation
- Responsibility based — a policy based on the responsibilities assigned to a business role
- Role based control — a policy based on job title.
- Time based – Temporary access provided, and Shift patterns can be incorporated to ensure staff can only access during their shift.
Expected Business Outcomes
We can create a solution to meet your needs whether it is 1:1 or 1:N matching.
User Guide