How to Solve the Strong Customer Authentication requirement within PSD2?
6 Jul 2018
The Second Payment Services Directive or PSD2 as it is commonly known was implemented in January of this year. The original Payment Services Directive (PSD) created a single market for payments processing in 2007.
Since then, the financial world has moved on significantly and with digitalisation and innovation, there have been many new entrants into the payments and banking arena offering a range of new services and often finding themselves outside of the scope of PSD.
PSD2 is a force for good for consumers by providing a level playing field for both the existing players and those new entrants to compete in whilst improving security and hoping to address the fast-growing problem of banking and payment fraud.
As long as the transaction is based on an official currency (but excluding crypto-currencies), the rules still apply even if one of the parties that process the transaction is located outside of the EU.
The Financial Conduct Authority (FCA) in the UK has summarised the main aims of the directive as:
- Contribute to a more integrated and efficient European Payments market
- Create a level playing field for payment service providers
- Promote the development and use of innovative online and mobile payments
- Make payments safer and more secure
- Protect consumers
- Encourage lower prices for payments processing.
What about the impact for citizens? In the most simple terms, the aims to 1) increase security by insisting on strong customer authentication and 2) the creation of a competitive environment helping innovation to flourish, will both mean better options in the end for consumers.
If we focus in on the often challenging area of strong customer authentication:
The directive defines the authentication part as “a procedure for the validation of the identification of a natural or legal person based on the use of two or more elements categorized as knowledge, possession and inherence that are independent.”
What does that mean practically?
- Knowledge = something you know — a passcode or PIN, for example
- Possession = something you have — a SIM card or a cashpoint card
- Inherence = something you are — biometric information, such as a finger scan
For remote transactions (internet & mobile) – unique authentication codes will link the transaction with the person making the payment and the transaction amount. A new Open API standard aims to provide access into both the banking customer’s account and the transactional data to make the basis for the payment provider to correctly tie these things together.
Just one of these elements on its own isn’t very secure. For instance, something you know such as a login passcode could be stolen and used by someone else. But combine that passcode with something you own, like a card reader, and it becomes stronger.
A number of companies are currently marketing their security systems as ‘multi-layer authentication’, whereas in reality they only offer two of the three layers. That’s certainly stronger than a single layer and meets with the requirements of the PSD2 Regulatory Technical Standards (RTS) to use at least 2 of the 3 layers, but doesn’t go as far as it could.
Using a 3-layer model with a biometric check is the only way to create a true non-repudiable transaction.
“For ultimate protection, you really need all three layers,” explains Ravi Ahluwalia, Deputy General Manager, Information Systems Group, “That means biometric technology is going to become increasingly important.”
Indeed, the role of biometrics in banking is expected to grow dramatically with Goode Intelligence predicting that by the end of 2020, 1.9bn bank customers around the world will be using biometrics, spanning from ATM withdrawals to mobile App logon to digital on-boarding.
For the “Inherence” layer, the question remains about which biometric tools can be both practical and easy to use whilst at the same time providing an acceptable level of security since there is generally a trade-off between these things. There is a big issue to consider around data-privacy when using methods for inherence in that some biometric data that can be captured without the consent of the individual could in itself be a security risk.
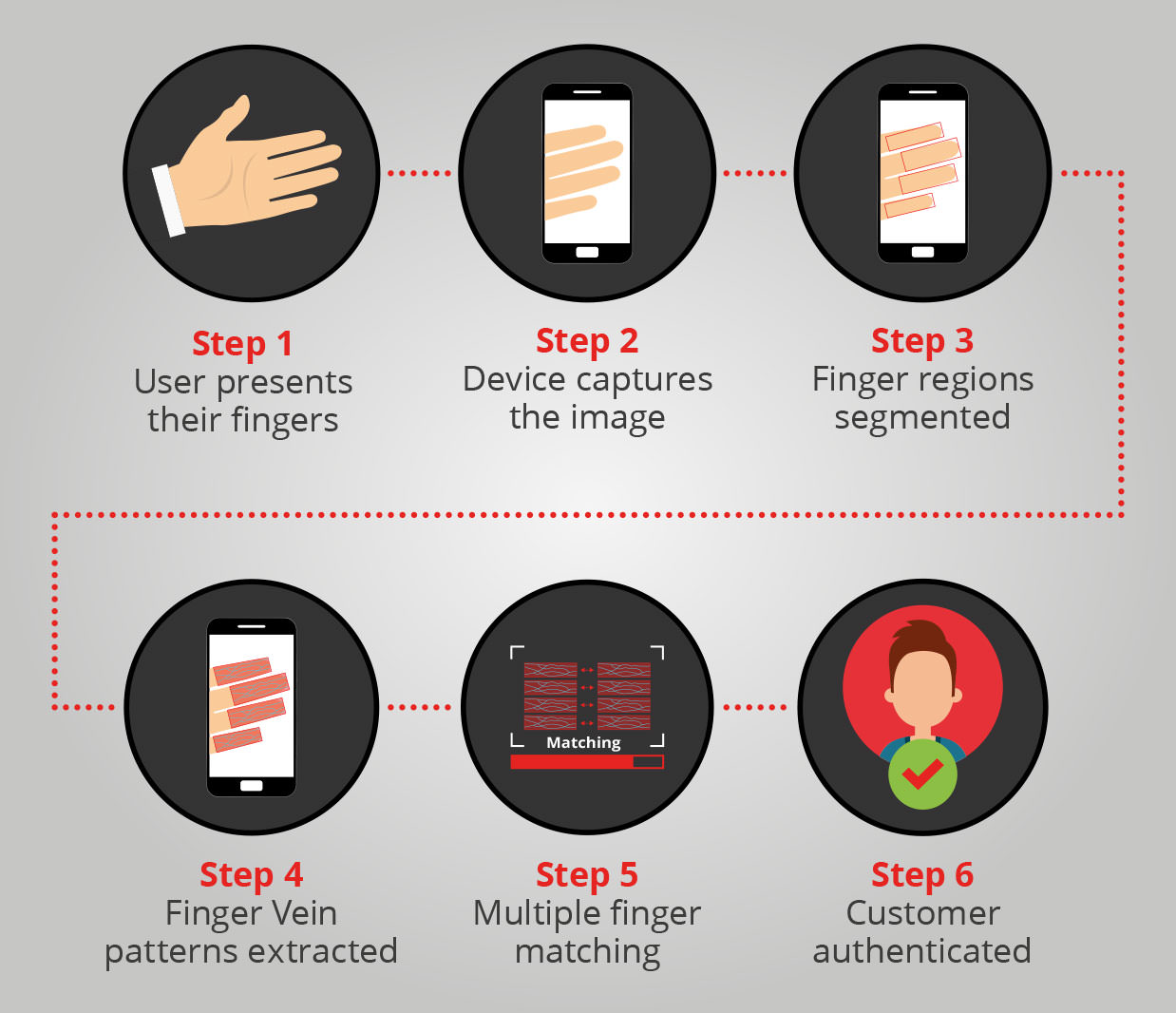
An example of just what’s possible with biometric scanning is VeinID from Hitachi, which enables customers to verify their identity simply by placing their finger on a vein scanner. The technology is incredibly secure, and combined with the other two layers of authentication, it could create the ultimate in customer protection helping to make light work of the RTS requirement.
The next generation of VeinID takes things to a whole new level of practicality and usability. Allowing finger vein data to be captured using a standard digital camera (e.g. a camera phone, PC or tablet), the ability for consumers to use privacy compliant biometrics in everyday transactions without any special devices or tokens being issued by a bank, will become a reality. Quicker than a selfie with no need to pose and none of the privacy concerns, this software solution can be integrated with ease into banking applications. The diagram shows the process flow for both access control and transaction authentication.
With the legislation now calling for ever more rigorous security, it seems increasingly likely that more companies will extend their offering to include biometrics like Hitachi’s VeinID.
